Use of end-to-end encryption
By default, 1:1 calls are end-to-end encrypted now. Therefore, a configured key backup as well as a verification of all self-used client devices is recommended (Important settings)
The decision whether a created room should be encrypted in this way must be well thought out and cannot be undone. If the room is large or public, checking all keys of all participants can take a lot of time. This manual check is done later on occasion and end-to-end encrypted conversations are started directly with blind trust for the time being.
If end-to-end encryption (E2EE) to interlocutor:inside in an unencrypted room is needed, click on the settings of the desired room (or in the room via “Room info” > “Room settings” in the upper right corner):
To do this, activate the Encrypted slider on the Security & Privacy tab:
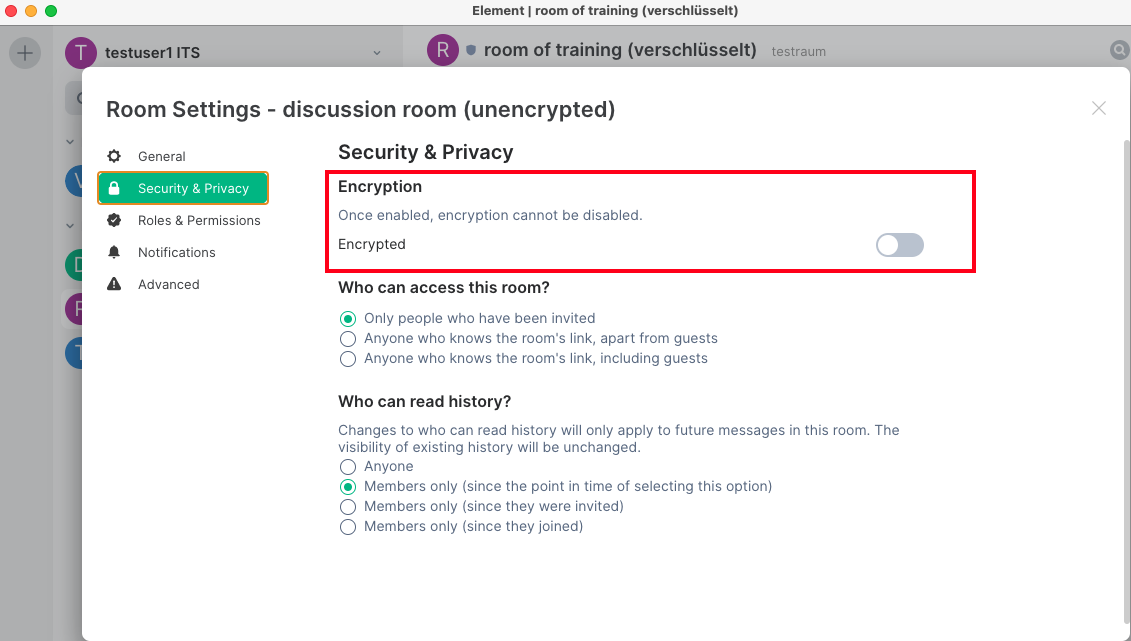
Confirm with OK. From now on only those involved in the conversation are able to read the messages. When no key protection has been set up in the settings before, do it now (see Important settings) to read earlier messages and those received in absence.
The encrypted exchange can begin now. To verify the correctness of the keys and to document this trustworthiness digitally, first unfold the sidebar by clicking on the person symbol in the upper right corner:
Click the contact person in the opening bar of the participants in the conversation:
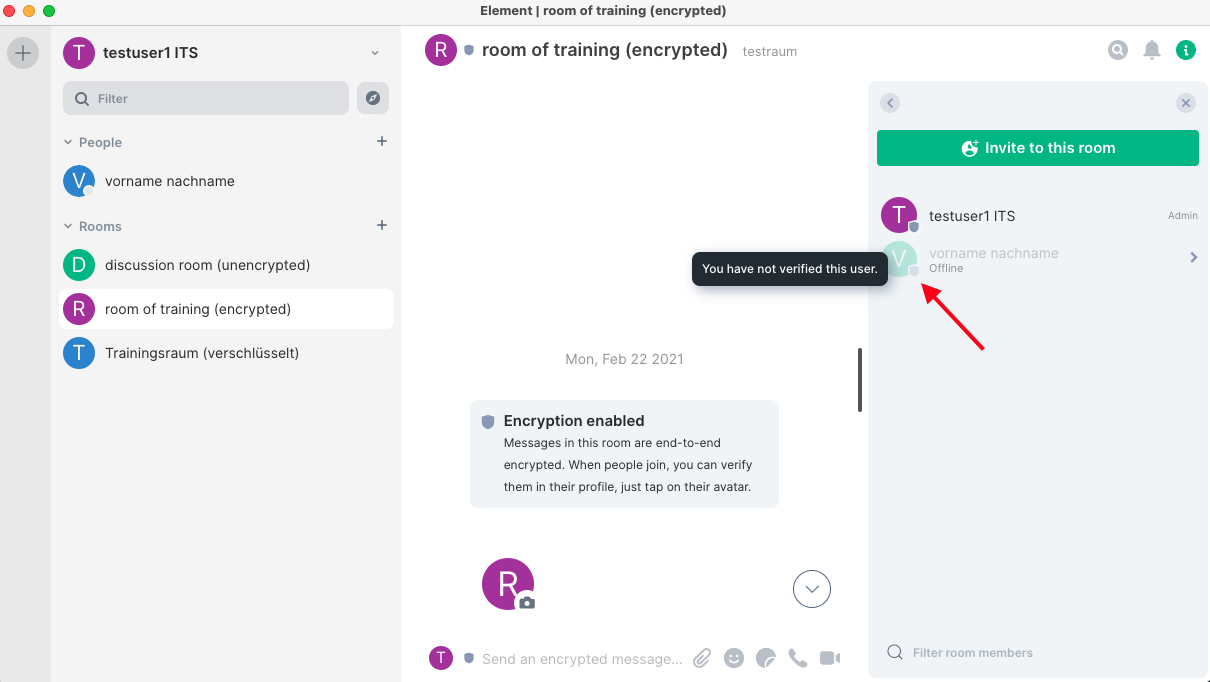
The bar shows the conversation person in detail now. Here a key verification is initiated by clicking on “Verify”. The other side is notified by clicking on “Start Verification”. After confirmation (see next picture) the “Verification by Emojis” starts.
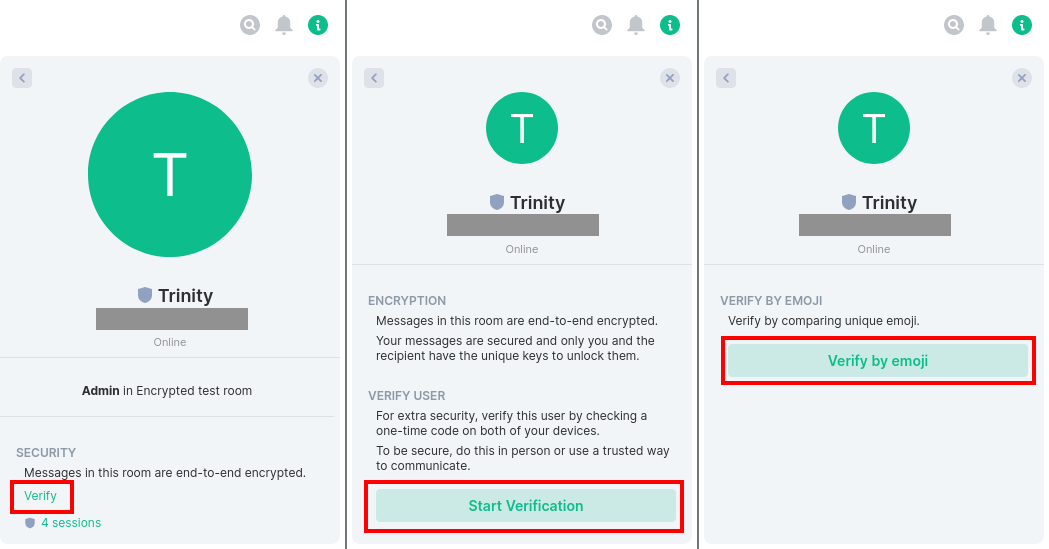
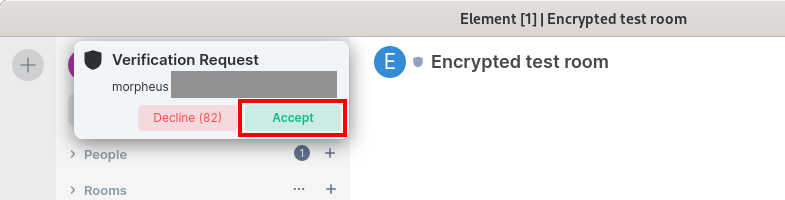
This verification should be done with the contact person by comparison (e.g. verbally via telephone, in the same room or other medium). Since this is not always easy, the trust can also be expressed first (otherwise the verification is asked again and again) and carried out on occasion (e.g. at the next meeting).
A detailed description of the topic is shown in this video by Prof. Plikat and in this Matrix blog article.
The adjustment itself is done via emoji images or QR codes, which look different depending on the device and icon pack. Also, the translation of all interface elements into German is not 100% available.
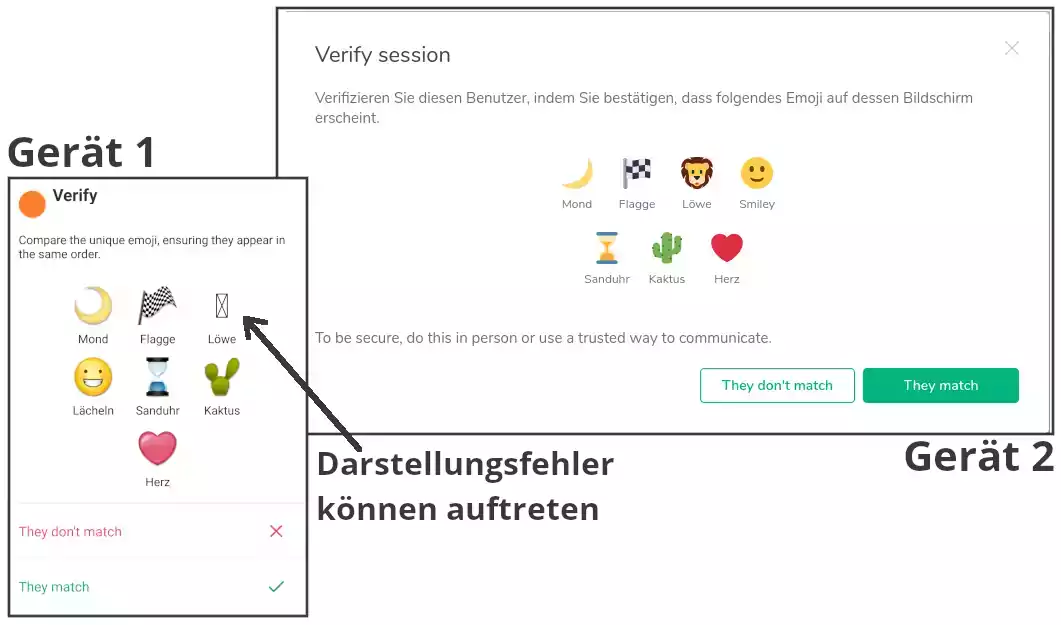
This is done analogously in rooms with several participants, each one individually.

The following symbols indicate the status of the encryption and the corresponding verification in the respective room rows:

At least one person in the room has not yet been verified.

There is at least one person in the room who has already been verified, but who in turn has opened further unverified sessions.

All persons in the room were verified.